Attribute Based Access Control Diagram
Attribute based access control is a model that evolved from rbac. It represents a point on the spectrum of logical access control from simple access control lists to more capable role based access and finally to a highly flexible method for providing access based on the evaluation of attributes.
The State Of The Union Of Authorization Axiomatics
Attribute based encryption is a type of public key encryption in which the secret key of a user and the ciphertext are dependent upon attributes e g.
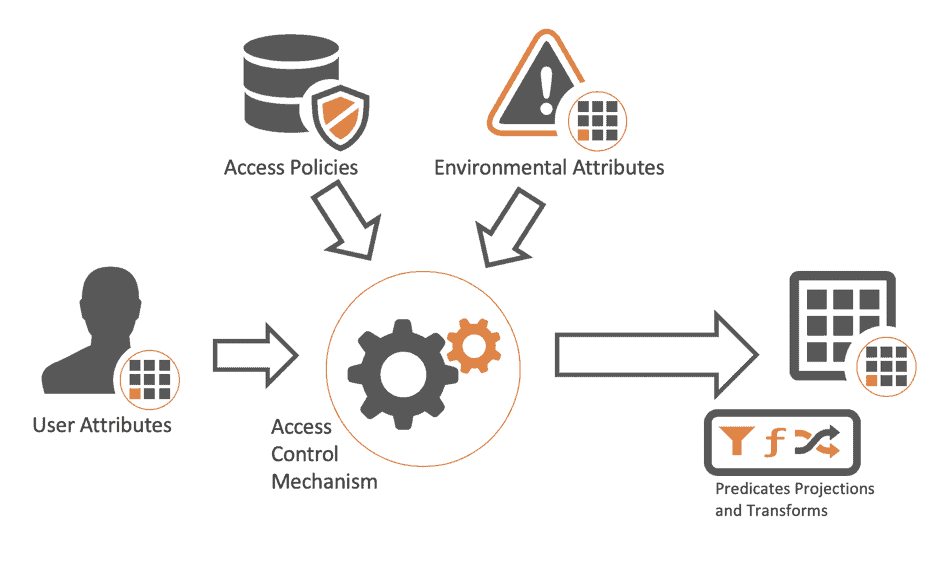
Attribute based access control diagram. Attribute based access control abac uses attributes as building blocks in a structured language that defines access control rules and describes access requests. Abac allows you to define access rules with a far finer granularity of access control relative to other models like role based rbac or access control list acl without losing any of the. Based approach to attribute based access control abac.
One approach to granting access to resources is to use attribute based access control abac to centrally govern and manage access to your aws resources across accounts. Jwt s claim based identifies attributes that can be used to enforce access controls at the api gateway. This guide discusses potential security risks facing organizations benefits that may result from the implementation of an abac system and the approach that the nccoe took in developing a.
Aws identity and access management iam allows customers to provide granular access control to resources in aws. This model is based on establishing a set of attributes for any element of your system. The concept of attribute based access control abac has existed for many years.
What is attribute based access control abac. A central policy defines which combinations of user and object attributes are required to perform any action. The country in which they live or the kind of subscription they have.
In such a system the decryption of a ciphertext is possible only if the set of attributes of the user key matches the attributes of the ciphertext. Attribute based access control abac also known as policy based access control for iam defines an access control paradigm whereby access rights are granted to users through the use of policies which combine attributes together the policies can use any type of attributes user attributes resource attributes object environment attributes etc. In november 2009 the federal chief information officers council federal cio.
Registration and access control are handled separately. Using abac enables you to simplify your authentication strategy by enabling you to scale your authorization. Attributes are sets of labels or properties that can be used to describe all the entities that must be considered for authorization purposes.
Rbac Vs Abac Access Control What S The Difference Dnsstuff
From Real World Identities To Privacy Preserving And Attribute
Use Attribute Based Access Control With Ad Fs To Simplify Iam
Attribute Based Access Control
2019 Scale Permissions Management With Attribute Based Access Contr
Attribute Based Access Control Beyond Roles Axiomatics
Access Control Concepts Identity Server 5 3 0 Wso2 Documentation
Cloud Computing Patterns Mechanisms Attribute Based Access
Role Based Access Control Vs Attribute Based Access Control How
Attribute Based Access Control
Attribute Based Access Control Model For Multimedia Social
Cdh6 2 Cloudera Search Attribute Based Access Control Part 2
Axiomatics Federal Named A Finalist In 2018 Astors Awards
Figure 2 From Comparison Of Attribute Based Access Control Abac
An Extended Attribute Based Access Control Model With Trust And
Rbac And Abac And Roles Oh My Identity Sander
Multi Tenant Attribute Based Access Control For Cloud
Https Nvlpubs Nist Gov Nistpubs Specialpublications Nist Sp 800 178 Pdf
Rbac And Abac And Roles Oh My Identity Sander
Fine Grained Attribute Based Access Control Model For Privacy
Webinar On Attribute Based Access Control Abac Authorizing Data
Role Based Access Control Vs Attribute Based Access Control How
Attribute Based Access Control In Web Applications Springerlink
Attribute Based Access Control Abac By Wentz Wu Cissp Issmp
Architecture For Attribute Based Access Control System Download
If Policy Is The New Perimeter Then Abac Make It Possible Ionic
Enforcing Fine Grained Access Control Policies To Meet Legal
Scheme Of Attribute Based Access Control Abac Model Download
Attribute Based Access Control Framework And Data Flow Diagram
Role Based Access Control Page 2 Blog Nextlabs Com
Intro To Attribute Based Access Control Abac Axiomatics
Pdf A Semantic Aware Attribute Based Access Control Model For Web
Enterspace Decisioning Service For Attribute Based Access Control
Https Nvlpubs Nist Gov Nistpubs Specialpublications Nist Sp 800 162 Pdf
System Model Of Attribute Based Access Control For Proxy Re
Attribute Based Access Control Glossary Definition Jericho Systems
Better Way To Add Extra Attributes In Rbac Role Based Access
Pdf Attribute Based Access Control Semantic Scholar
Posting Komentar
Posting Komentar