Attribute Based Access Control Model
In aws these attributes are called tags. In this paper we propose a cloud based ehr model that performs attribute based access control using extensible access control markup language.
Attribute Based Access Control
An attribute based access control model in rfid systems based on blockchain decentralized applications for healthcare environments.
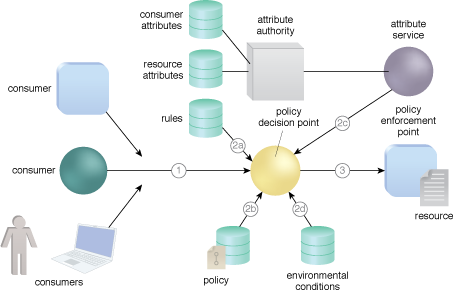
Attribute based access control model. Attribute based access control is a model that evolved from rbac. Attribute based access control abac is an authorization strategy that defines permissions based on attributes. User attributes attributes associated with the application or system to be accessed and current environmental conditions.
Computers 2019 8 57. Attribute based access control abac also known as policy based access control for iam defines an access control paradigm whereby access rights are granted to users through the use of policies which combine attributes together the policies can use any type of attributes user attributes resource attributes object environment attributes etc. Note that from the first issue of 2016 mdpi journals use article numbers instead of page numbers.
It represents a point on the spectrum of logical access control from simple access control lists to more capable role based access and finally to a highly flexible method for providing access based on the evaluation of attributes. This refers to the character of elements within the network. An example of abac would be allowing only users who are type employees and have department hr to access the hr payroll system and only during business hours.
A central policy defines which combinations of user and object attributes are required to perform any action. The concept of attribute based access control abac has existed for many years. This model comprises of several components.
Our ehr model focused on security performs partial encryption and uses electronic signatures when a patient s document is sent to a document requester. Attribute based access control abac uses attributes as building blocks in a structured language that defines access control rules and describes access requests. Show more citation formats.
In november 2009 the federal chief information officers council federal cio. Attribute based access control is a model inspired by role based access control. This model is based on establishing a set of attributes for any element of your system.
Abac can control access based on three different attribute types. Attributes are sets of labels or properties that can be used to describe all the entities that must be considered for authorization purposes. Controlling who accesses information and under what conditions enables the right people to access the right information at the right time.
Tags can be attached to iam principals users or roles and to aws resources. Attribute based access control abac is a security model that allows individuals to define the rules of who accesses information. The basis of the attribute based access control is about defining a set of attributes for the elements of your system.
Attribute Based Access Control
Attribute Based Access Control Abac By Wentz Wu Cissp Issmp
Https Nvlpubs Nist Gov Nistpubs Specialpublications Nist Sp 800 162 Pdf
Get Started Now With Attribute Based Access Control Abac
Attribute Based Access Control Beyond Roles Axiomatics
What Is Abac For Aws Aws Identity And Access Management
Rbac Vs Abac Access Control What S The Difference Dnsstuff
An Extended Attribute Based Access Control Model With Trust And
32 Attribute Based Access Control In Hyperledger Fabric 2 0 Youtube
Comparison Of Attribute Based Access Control Abac Model And Rule
Enterspace Decisioning Service For Attribute Based Access Control
Use Attribute Based Access Control With Ad Fs To Simplify Iam
Attribute Based Access Control
Figure 2 From Comparison Of Attribute Based Access Control Abac
Fine Grained Attribute Based Access Control Model For Privacy
System Model Of Attribute Based Access Control For Proxy Re
Attribute Based Access Control
Cdh6 2 Cloudera Search Attribute Based Access Control Part 2
What Are The Advantages Disadvantages Of Attribute Based Access
Attribute Based Access Control In Web Applications Springerlink
Scheme Of Attribute Based Access Control Abac Model Download
What Is A Suggested Roadmap Towards Implementation Of A Simple
Attribute Based Access Control Abac Axiomatics
Role Based Access Control Vs Attribute Based Access Control How
Role Based Access Control Vs Attribute Based Access Control How
Devise An Attribute Based Access Control Plan That Won T Affect
Attribute Based Access Control Models And Beyond Ppt Video
If Policy Is The New Perimeter Then Abac Make It Possible Ionic
Rbac Vs Abac Access Control What S The Difference Dnsstuff
An Extended Attribute Based Access Control Model With Trust And
Attribute Based Access Control Model For Multimedia Social
Attribute Based Access Control
Pdf Attribute Based Access Control Semantic Scholar
Role Based Access Control Vs Attribute Based Access Control How
Attribute Based Access Control Abac In A Microservices
Attribute Based Access Control With A Graph Database Lean Java
Cloud Computing Patterns Mechanisms Attribute Based Access
Attribute Based Access Control Glossary Definition Jericho Systems
Posting Komentar
Posting Komentar