Attribute Based Access Control Example
Role based access control rbac and attribute based access control abac are two ways of controlling the authentication process and authorizing users. The concept of attribute based access control abac has existed for many years.
 Figure 1 From On Attribute Based Access Control Scheme In Cloud
Figure 1 From On Attribute Based Access Control Scheme In Cloud
Attribute based access control abac is an authorization strategy that defines permissions based on attributes.

Attribute based access control example. In aws these attributes are called tags. Then you will probably find attribute based access control very useful. Attribute evaluation then enables effective policy based authorization.
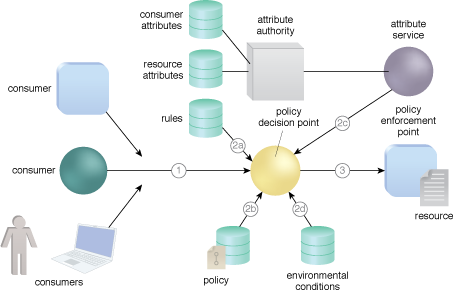
The policy regulating access to services is therefore defined over attributes and credentials provided by clients. Aws identity and access management iam allows customers to provide granular access control to resources in aws. Attribute based access control restricts access to server service depending on the attributes and credentials that the requesting client discloses to the server.
A policy states that all users belonging to the sales department should have read access to proposals sent to customers within the sales region to which the user belongs. It represents a point on the spectrum of logical access control from simple access control lists to more capable role based access and finally to a highly flexible method for providing access based on the evaluation of attributes. In november 2009 the federal chief information officers council federal cio.
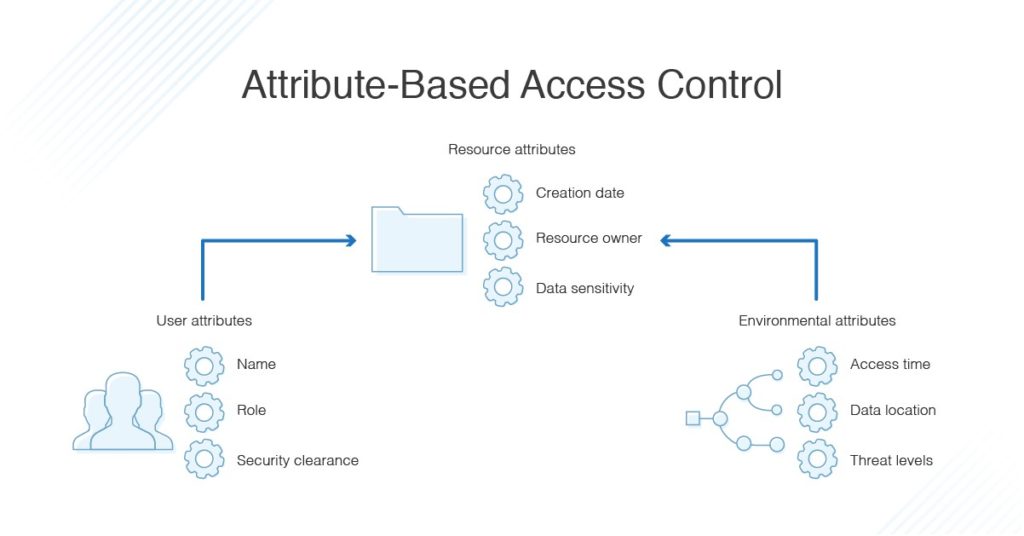
User attributes attributes associated with the application or system to be accessed and current environmental conditions. What is attribute based access control abac any access request will have four elements subject resource action and. Attribute based access control abac also known as policy based access control for iam defines an access control paradigm whereby access rights are granted to users through the use of policies which combine attributes together the policies can use any type of attributes user attributes resource attributes object environment attributes etc.
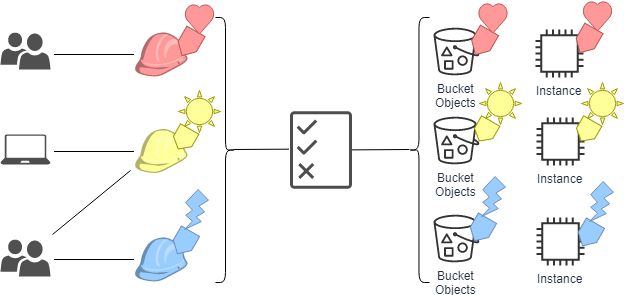
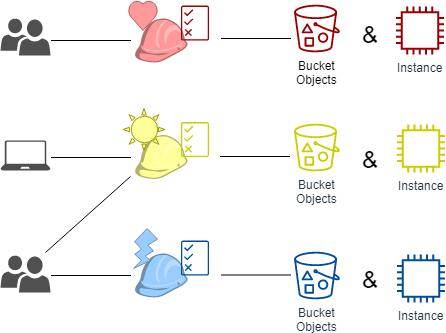
Using abac enables you to simplify your authentication strategy by enabling you to scale your authorization. One approach to granting access to resources is to use attribute based access control abac to centrally govern and manage access to your aws resources across accounts. An example of abac would be allowing only users who are type employees and have department hr to access the hr payroll system and only during business hours.
The primary difference between rbac and abac is rbac provides access to resources or information based on user roles while abac provides access rights based on user environment or resource. Tags can be attached to iam principals users or roles and to aws resources. Abac can control access based on three different attribute types.
Let s consider this example.
 Figure 5 From Guide To Attribute Based Access Control Abac
Figure 5 From Guide To Attribute Based Access Control Abac
 Rbac Vs Abac Access Control What S The Difference Dnsstuff
Rbac Vs Abac Access Control What S The Difference Dnsstuff
 What Are The Advantages Disadvantages Of Attribute Based Access
What Are The Advantages Disadvantages Of Attribute Based Access
 Attribute Based Access Control Glossary Definition Jericho Systems
Attribute Based Access Control Glossary Definition Jericho Systems
 An Extended Attribute Based Access Control Model With Trust And
An Extended Attribute Based Access Control Model With Trust And
 Cloud Computing Patterns Mechanisms Attribute Based Access
Cloud Computing Patterns Mechanisms Attribute Based Access
 Figure 1 From Attribute Based Access Control Semantic Scholar
Figure 1 From Attribute Based Access Control Semantic Scholar
Https Nvlpubs Nist Gov Nistpubs Specialpublications Nist Sp 800 162 Pdf
 Attribute Based Access Control Beyond Roles Axiomatics
Attribute Based Access Control Beyond Roles Axiomatics
 What Is Abac For Aws Aws Identity And Access Management
What Is Abac For Aws Aws Identity And Access Management
 Rbac And Abac And Roles Oh My Identity Sander
Rbac And Abac And Roles Oh My Identity Sander
 What Is Abac For Aws Aws Identity And Access Management
What Is Abac For Aws Aws Identity And Access Management
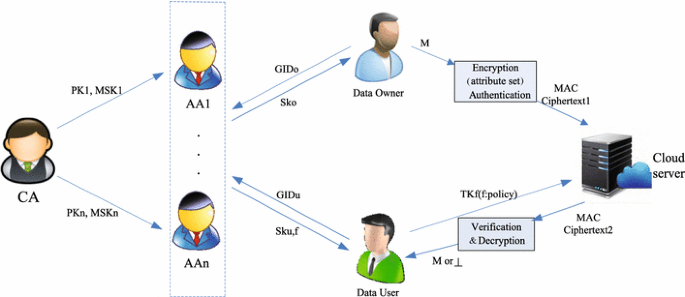 Succinct Multi Authority Attribute Based Access Control For
Succinct Multi Authority Attribute Based Access Control For
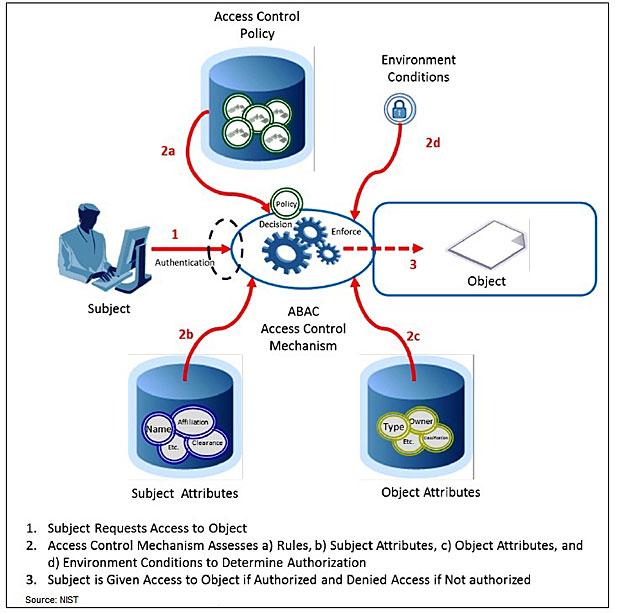 Nist Guide Aims To Ease Access Control Bankinfosecurity
Nist Guide Aims To Ease Access Control Bankinfosecurity
 The Benefits Of Fine Grained Dynamic Authorization An
The Benefits Of Fine Grained Dynamic Authorization An
 Role Based Access Control Vs Attribute Based Access Control How
Role Based Access Control Vs Attribute Based Access Control How
 Attribute Based Access Control For Data Protection Webinar May 8
Attribute Based Access Control For Data Protection Webinar May 8
 Authorizing Resources Based On Who Created Them Michael C Good
Authorizing Resources Based On Who Created Them Michael C Good
 Role Based Access Control Vs Attribute Based Access Control How
Role Based Access Control Vs Attribute Based Access Control How
 Rbac And Abac And Roles Oh My Identity Sander
Rbac And Abac And Roles Oh My Identity Sander
 What Is A Suggested Roadmap Towards Implementation Of A Simple
What Is A Suggested Roadmap Towards Implementation Of A Simple
 Attribute Based Access Control
Attribute Based Access Control
 1 Rabac Role Centric Attribute Based Access Control Mmm Acns
1 Rabac Role Centric Attribute Based Access Control Mmm Acns
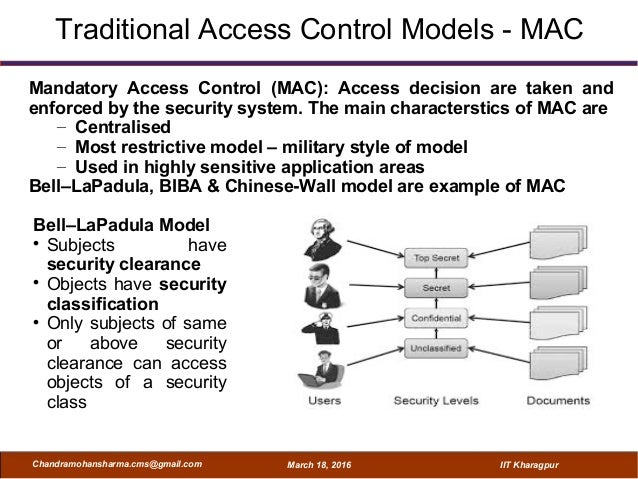 Attribute Based Access Control
Attribute Based Access Control
 Enterprise Abac Scenario Example Download Scientific Diagram
Enterprise Abac Scenario Example Download Scientific Diagram
 An Extended Attribute Based Access Control Model With Trust And
An Extended Attribute Based Access Control Model With Trust And
Attribute Based Access Control Abac Axiomatics
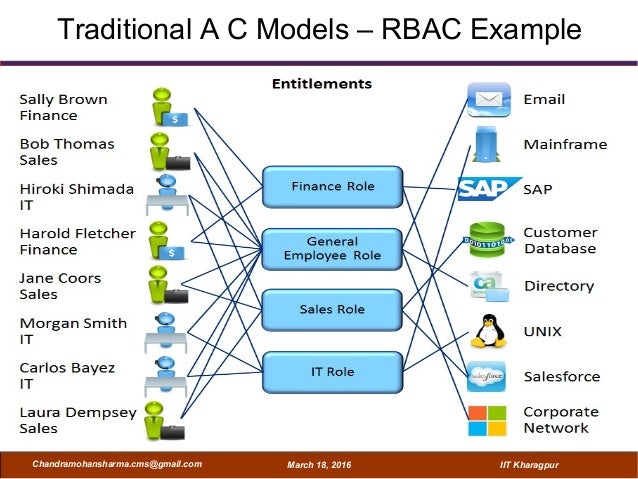 Attribute Based Access Control
Attribute Based Access Control
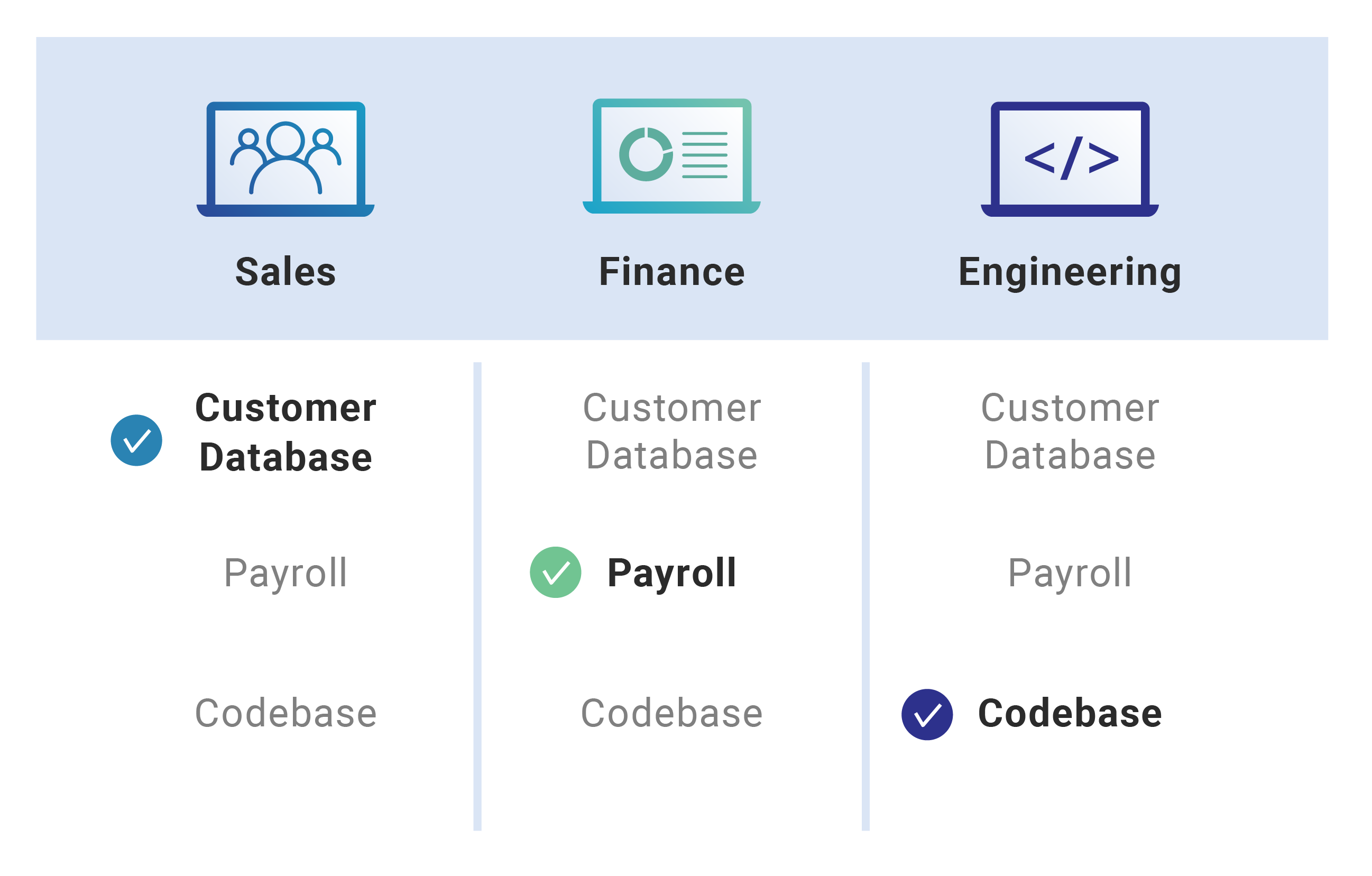 What Is Role Based Access Control Rbac Cloudflare
What Is Role Based Access Control Rbac Cloudflare
 Role Based Access Control Vs Attribute Based Access Control How
Role Based Access Control Vs Attribute Based Access Control How
 Get Started Now With Attribute Based Access Control Abac
Get Started Now With Attribute Based Access Control Abac
Https Nvlpubs Nist Gov Nistpubs Specialpublications Nist Sp 800 178 Pdf
Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcr1gpar2hpvezg3vd2o7has Va3t Jpaxqjcgnenwilfk Xewaf Usqp Cau
 Attribute Based Access Control With A Graph Database Lean Java
Attribute Based Access Control With A Graph Database Lean Java
 Multi Tenant Attribute Based Access Control For Cloud
Multi Tenant Attribute Based Access Control For Cloud
 Get Started Now With Attribute Based Access Control Abac
Get Started Now With Attribute Based Access Control Abac
 Webinar On Attribute Based Access Control Abac Authorizing Data
Webinar On Attribute Based Access Control Abac Authorizing Data
 Attribute Based Access Control Ppt Download
Attribute Based Access Control Ppt Download
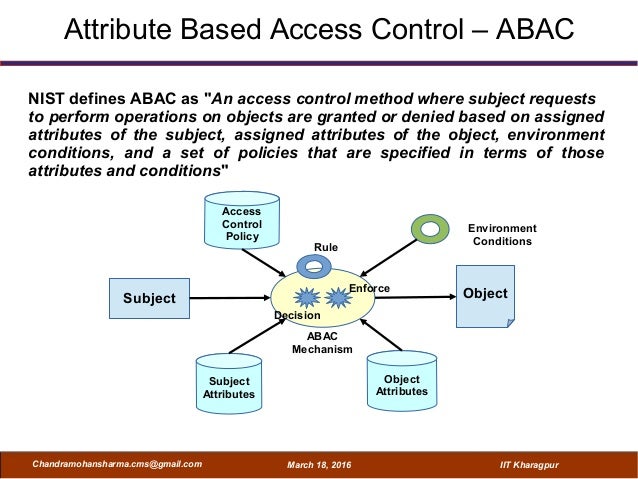 Attribute Based Access Control
Attribute Based Access Control
Posting Komentar
Posting Komentar